Deliverability
What is phishing?
To know how to protect yourself and you audience, you need to understand what phishing is and how to recognize it. Keep reading and we’ll help you avoid any issues.

PUBLISHED ON
Despite the advancement in technical security measures, phishing remains one of the cheapest and simplest ways for cybercriminals to gain access to sensitive information. As easy as clicking a link, victims of phishing are susceptible to sharing private information and put themselves at risk of identity theft.
To know how to best protect yourself, you need to understand what a phishing attack is, the different types hackers use, and how to recognize them if and when they land in your inbox. Keep reading and we’ll help you avoid any unnecessary security issues from phishing attacks.
Table of content
How do phishers find the email addresses they want to target?
Spray and pray
Spear phishing
Clone phishing
Whaling
Email spoofing
Pharming
Typosquatting
Clickjacking
Angler phishing
Smishing
Vishing
Quishing
AI phishing
The sender address
Misspelled domain names
Bad grammar and spelling
Suspicious attachments/links
Sense of urgency
The message is too good to be true
Email authentication
08
Summary
What is a phishing email attack?
Phishing is an online scam where criminals impersonate legitimate entities to trick victims into sharing sensitive information or installing malware.
The term “phishing” is a play on the word “fishing” since in both cases someone throws out bait and waits for users or fish to “bite”. Most often hackers do this via malicious emails that appear to be from trusted senders by including a link that will seem to take you to the company’s website. Once you fill in your data, that sensitive information can be stolen.
That data can be sensitive information, such as login credentials (email and password), financial data (credit card details or online banking credentials) or even personal data (date of birth, address or social security number). Phishing is considered a type of social engineering attack because it relies on human failures instead of hardware or software.
A brief history of phishing
The first example of phishing dates back to the mid-1990s, when an attempt to steal AOL user names and passwords was made using tools like AOHell. Despite many warnings from AOL, the attacks were successful, since phishing was a brand-new concept and not something people had seen before.
Following the initial AOL attacks, many early phishing scams came with obvious signs off illegitimacy - including strange spelling, weird formatting, pixelated images and messages that often didn't make a lot of sense.

An example of an early phishing email targeting AOL users
Some phishing campaigns remain easy to recognize (we’ve all received the email from the Nigerian Prince who wants to leave his small fortune to you), but others have become so advanced that it's nearly impossible to tell them apart from real emails. This is because phishers have evolved along with new technical capabilities. Scams have now spread to social media, messaging services and apps.
If you check email or social media sites from your phone, you may become an easy target. Since the email interface on mobile phones is a lot smaller than on a computer, it makes it more difficult to flag signs of phishing, such as seeing the full URL.
Ultimately, if you have an email address, it is all but guaranteed that you have received a phishing message in your inbox at least once.
How does a phishing attack work?
A basic phishing attack attempts to trick a user into entering personal details or other confidential information. In the US, around 10 billion emails are sent every single day making for an ideal channel for cybercriminals. Imagine if even 1% of those emails are a scam, and 1% of those work. That is one million successful attempts every day!
We can assure you that it’s likely far more than 1% of scam emails, but we’d like to help you make sure that far less than 1% of those are successful.
A phishing attack can have a specific target, such as people using a specific product, or can be scattershot, going after the general public with fake contests and prizes. In both cases, the victims are asked to enter their names, email addresses and, in some cases, passwords and bank details.
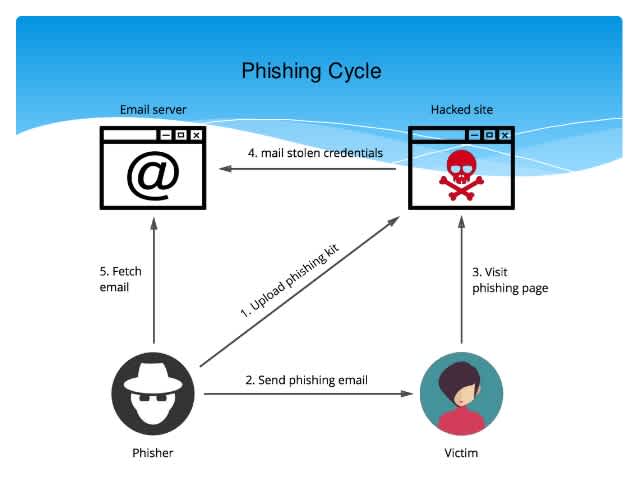
Another option is that the email contains a malicious attachment that you will be requested to download. In many cases, the malicious payload will be hidden inside a Microsoft Office document which requires the user to enable macros to run. Once you try to open the document you may be asked to update your software or provide certain permissions to allow the document to be viewed properly. But if you agree with any of this, you are likely opening yourself up to a severe security breach.
How do phishers find the email addresses they want to target?
There are a lot of ways for phishers to retrieve your email address and link it to a service you are using, and this can happen without your knowledge or the knowledge of the service provider.
Here are some of the most common:
Searching over the web for the @ sign. Spammers and cybercriminals use advanced tools to scan the web and harvest email addresses. If you ever posted your email address online, a spammer will find it.
Cybercriminals use tools to generate common usernames (using the first letter of a first name and a common last name) and combine them with common domains. These are typically used to crack passwords.
Spammers can buy email lists and this can be done legally and illegally. Make sure you read the privacy policy carefully when you provide your email anywhere. Even if GDPR is protecting you, you need to protect yourself as well.
Phishers are also able to find what each service provider would ask you to do as a client and then find a vulnerability to figure out if you are a client. For example, in the case of ESPs, scammers can check your public DNS records (SPF, CNAME, TXT) and try to find information that can link it to the ESP you use.
Now we know the basics of what phishing is, its history, and how it works, we can explore some of the most common types of phishing.
What are the different types of phishing attacks?
We can assume that almost everyone has already been the victim of a phishing email attack or landed on a suspicious website. There are many types of attacks and hackers are becoming more and more creative every day, so we need to stay on top of some of the new methods being used to easily flag it as risky before getting caught.
Below, we have listed some of the most common attacks that are used today.
Spray and pray
The 'spray and pray' approach is the least complex type of phishing attack, where one message is mass-mailed to millions of users. These messages claim urgency one way or another. Either by stating that there is an “important” message from your bank or a popular service, or that “you've won the latest iPhone and need to claim it now.”
Depending on the hacker’s technical abilities, spray & pray attacks may not even involve fake web pages - victims are often just told to respond to the attacker via email with sensitive information. These attacks are mostly ineffective but can be sent to a massive amount of email addresses. It doesn’t take many victims to be deemed a success for the phisher.
Spear phishing
Spear phishing is more advanced. Unlike “spray and pray”, which sends to a mass list, ‘spear phishing’ targets specific groups with a more personalized message. Phishers will, for instance, target users of a specific brand and will design the email to replicate that brand. In fact, they can target anything from a specific organization to a department within that organization. Sometimes, specific individuals are targeted to ensure the greatest chance that the email is opened and more personal information is acquired. The highest profile cyber-attacks typically come from this type of approach.
The most common spear phishing message will be designed to look as if someone wants you to change your password because of an issue on the service side. In this case, the message will appear to be a legit message - as close as possible to the original sent by the brand, and will redirect you to a similarly branded page. These attacks more effective because they are well planned.
Clone phishing
Clone phishing emails will look identical to an email you previously received. However, in this case, the new email will be sent from a spoofed address that resembles the original one. For example help@appplehelp.com instead of help@apple.com (notice the three “P”s).
Within the content, the only difference between the cloned email and the original email is that the links and/or attachments have been changed, likely directing you to malicious sites or software. As the email looks really close to the original one the recipients are more likely to fall for this sort of attack.
Whaling
This is an attack targeting a smaller group of high-profile individuals, such as board members or members of the finance or IT team. The email can appear to be coming from a trusted source, such as the CEO of your company.
This attack is harder to create because hackers will firstly need to find the right targets, and then have enough information on how to impersonate the CEO. However, the rewards are potentially greater: CEOs and other C-level executives have more information and greater levels of access than junior employees. Inboxes like GSuite can help prevent this by assigning profile pictures to internal colleagues’ email addresses, but also through features like whitelisting.
Email spoofing
Email spoofing attacks are mostly “urgent” requests from a brand or a brand’s senior staff member. These emails are social engineering tactics to fool other staff members or users into giving their bank account details or making a donation.
A lot of popular service providers in the software space become victims to such attacks. Here’s an example of a phishing email sent from someone trying to impersonate WordPress:

Source: 360 Total Security
Once you have clicked on a link or any of the buttons you will be redirected to a fake page created to collect your information.
Pharming
This method of phishing would require the hacker to create an identical copy of a website by exploiting vulnerabilities in the domain name system and match the URL with the IP behind it. If successful, phishers would be able to redirect the traffic from a real site to a fake one.
This is possibly the most dangerous type of phishing attack, because DNS records are not controlled by the end-user and it is harder to defend yourself against this attack.
Typosquatting
Typosquatting is similar to pharming, except phishers don’t have to completely impersonate the domain they want to spoof. The URL will look genuine but with a slight difference. The goal is to take advantage of typos when users enter URLs. For instance, they might:
Misspell the legitimate URL by using letters that are next to each other on the keyboard;
Swap two letters around;
Add an extra letter;
Swap letters that sound the same in some cases - “n” and “m”, for example.
Clickjacking
This type of attack means that hackers are placing clickable content over legitimate buttons. For example, an online shopper might think they are clicking a button to make a purchase but will instead download malware.
Angler phishing
Nowadays, everything happens on social media, including phishing attacks. For example, you might receive a message with a link asking you to “Vote for me” or “Do you remember your time in Paris?” that redirects you to the Facebook login page after you click on it. Strange, right?
However, many people assume it’s just a system glitch and will enter their username and password anyway. But this new page is not really Facebook, and scammers now have your account details…
Some attacks are easier to spot, such as Facebook or Twitter bots sending you a private message containing a shortened URL. This URL likely leads to an empty page or one with suspicious content.
New attacks using social media continue to emerge, and some of them are playing a longer game. For example, they may be pretending to be someone else on the internet, which is not that hard to do with so many public images. Over time, these fake profiles may send you legitimate messages along with phishing messages to capture more information about you.
Smishing
Now that nearly everyone has a smartphone in their pocket, and RCS becoming an increasingly popular communication channel, most of the world is even more vulnerable to phishing attacks via SMS or any other messaging apps. An SMS phishing attack works mostly in the same way as an email attack, presenting the victim with content as an incentive to click through to a malicious URL.
The SMS are typically short and relevant to you in some way, in order to grab your attention and get you act quickly without thinking. Because of the plain text nature of SMS, and the ease of phone number spoofing, it is more difficult to spot. After the link in the SMS is clicked, the attack works in the same way as with email.
Another type of phishing on mobile devices is done through suspicious apps that are downloaded from unauthorized sites. The app may contain scripts that, once opened on your device, can access all your data. All your passwords can be accessed and if you have saved your bank or credit card details, they will be exposed as well.
Vishing
Vishing (short for voice phishing) is where attackers use phone calls to trick victims into giving away sensitive information. Just like phishing emails, vishing relies on social engineering – the art of manipulation. Vishing attackers often impersonate trusted entities like your bank, credit card company, or even the government. They might claim there's suspicious activity on your account, a problem with your recent purchase, or an urgent issue that requires immediate action.
Emails can play a role in vishing attacks, but not in the way you might think. Vishing attackers don't necessarily need to send emails first. However, they may use email as a springboard to a vishing attempt. For instance, you might receive a seemingly legitimate email that appears to be from your bank, warning you about fraudulent activity. The email might then pressure you to call a specific phone number to resolve the issue. This phone number, however, could be linked to the vishing attacker, waiting to steal your personal details over the phone.
Quishing
Have you ever scanned a QR code to access a website or download a file? If so, be cautious –QR phishing is a relatively new phishing attack that exploits the convenience of QR codes.
Scammers create fake QR codes that look legitimate. However, when scanned, victims are redirected to phishing websites designed to steal personal information. These fake sites might appear to be from your bank, a popular shopping platform, or even a social media service. Once you enter your login credentials or other sensitive data, the scammer has what they need to commit fraud or wreak havoc on your online accounts.
Quishing attacks are particularly dangerous because QR codes themself don't reveal their destination. Unlike a suspicious email link, a QR code doesn't show the underlying URL. This makes it easy for scammers to hide their true intentions and trick unsuspecting users into scanning a malicious code.
AI phishing
According to The State of Phishing 2024, there’s been a 1200% increase in phishing emails reported since generative AI such as ChatGPT landed on the scene in 2022.
Why such a sharp increase? AI phishing attacks leverage artificial intelligence to make the phishing emails more convincing and personalized. A bad actor could use AI algorithms to analyze vast amounts of data on a target segment, such as social media profiles, online behavior, and publicly available information which allows them to create personalized campaigns.
How to recognize a phishing attack
There are a few things you need to pay attention to whenever you come across a suspicious looking email or website seems. While some phishing campaigns are created to appear authentic, there are always some key clues to help spot them. Let’s have a look over some of the things that may show you if you are being a victim of a phishing attack.
The sender address
Check if you have ever received something from the same sender. If the phisher was smart enough, they will mask the sender address well, and the difference could be only one letter, so you may not even see it if you don’t take a closer look.
Misspelled domain names
If you have received a message that looks to be from an official company account (something like “support@mailjet-com.com”) be sure to confirm that this is the proper email domain for this company. Even if the message looks legitimate, with proper spelling and grammar, the correct formatting and the right company logo, it could still be a fraudulent account.
One clue is to check if the domain is slightly different than usual (like adding a suffix to a domain name). More importantly though, most legitimate brands will never ask you to communicate personal information by email.
Bad grammar and spelling
Many phishing attacks are not very well planned, especially “spray and pray” attacks, and the messages may contain spelling and grammar mistakes. Official messages from any major organization are unlikely to contain bad spelling or grammar, so badly written messages should act as an immediate indication that the message might not be legitimate.
Suspicious attachments/links
It's quite common for email phishing messages to ask the user to click on a link to a fake website designed for malicious purposes. The URL will look legitimate, but there will be small errors like missing or replaced letters.
If the message seems odd, it is always smart to take a second to examine the link more closely, by hovering the pointer over it to see if the web address is different than the real one. You can always contact the brand using their public email address or phone number to double check before clicking anything suspicious.
Cybercriminals often use PDF files to deliver malicious content to unsuspecting recipients, making people wary of opening attachments – especially if they are not expecting them. Here are some alternatives to PDFs you can try in future campaigns.
Sense of urgency
Many phishing attacks contain messages that warn of issues with your account, or problems with your payment. This is because the scammers are trying to make you act quickly without thinking too much. In these cases, it is even more important to double check the links in the message and the sender address.
The message is too good to be true
We’re sorry to break your bubble, but any message claiming that you have won a voucher or a prize is most likely a phishing attack. We’re sure it will require a bit more work than just putting in your personal information into a website, so you need to be super cautious and check all the key giveaways.
But hey, if you actually did win a prize, congrats!
What to do if you become a victim of a phishing attack?
If you’ve been the victim of a phishing attack, the first thing to do is change all of your passwords immediately. It is a good idea to not only change the password for the service the phisher may be impersonating, but all passwords. It’s alarming what a phisher can do with just one login credential. Consider using a password manager in the future to lower the risk, and make sure you have an antivirus solution with secure web browsing features installed and up to date.
Also, it’s always good to reach out to the service provider that was mimicked in the phishing attack and follow any additional instructions from them.
How to mitigate phishing attacks
There are some preventative measures that you can take to avoid phishing attacks or at least mitigate them. Here are some ideas:
Use your own links: If you are accessing websites daily or even weekly, it is better to use bookmarks for those sites. This is the only way to guarantee you land on the legitimate site. So even if you receive a notification, from say your bank, it is much safer to access your account via a bookmark than following a link.
Use Browser Extensions: Install or activate a web tool that identifies malicious sites for you so you know the website you find is legitimate. Example: Signal Spam plugin.
Install antivirus systems: Antivirus systems allow you to check if there is malware in a file before you open it, and potentially corrupt your computer.
Be Suspicious! Build a positive security culture at your company: On the internet, it is not a bad thing to be suspicious. Of course, some things are harder to check and need more technical knowledge, but you can do at least the most common steps.
Train your staff: If you are a security specialist, it is a smart idea to conduct regular security training for your employees to best recognize a phishing attack and what to do in such case.
Test the effectiveness of the training: Simulated phishing attacks will help you determine the effectiveness of the staff awareness training, and which employees might need further education. Plus, a little non-malicious phishing among friends can be fun.
Use 2-factor authentication whenever possible: If criminals steal your credentials, they will still not be able to use them without the second authentication means (SMS, authentication app, hardware token, etc.).
Email authentication
As an email sender you have two goals to defend. Your own sender reputation and security, and the security and data protection of your customers. This is where email authentication comes into play.
Email authentication is the process of verifying the legitimacy of an email sender and the integrity of their message(ing). The three standard email authentication protocols senders should be implementing are:
SPF (Sender Policy Framework)
DKIM (DomainKeys Identified Mail)
DMARC (Domain-based Message Authentication, Reporting, and Conformance).
They work in conjunction to validate a sender's identity, prevent email spoofing and phishing attacks, and improve overall security and email deliverability. What’s more, as of February 2024, both Gmail and Yahoo made email authentication compulsory for brands sending bulk email (5000+ a day) in an attempt to combat the increasing security threat to our inboxes.
If you’d like to find out more about these changes, we recently sat down with Yahoo’s Senior Director of Product, Marcel Becker, Google’s Director of Product Anti-Abuse and Safety, Anu Yamunan, and Sinch Mailgun’s Vice President of Deliverability, Kate Nowrouzi. You can see what they had to say below:
Summary
It might have been around for almost twenty years, but phishing continues to be a threat for two reasons - it's simple to carry out and it works. So, if you come across a pop-up message or suspicious emails from someone you don’t know (a desperate prince, maybe?) or a brand you don’t recognize... don’t click on it! You don’t want to leak your information to some hacker on the other side.
Also, if you’re unsure on how to authenticate your domain and further protect yourself and your subscribers from phishing attacks, we’ve put together some detailed documentation on how to set up both SPF and DKIM.








